
- Jun 9, 2025
- 8 minutes
-
 Andre Bittencourt
Andre Bittencourt
Navigating today’s digital landscape, CIOs and CTOs face a critical challenge: balancing cloud innovation with the imperatives of data sovereignty. For EU enterprises, reliance on US-based hyperscalers presents multifaceted risks. Legal uncertainties persist due to legislation like the US CLOUD Act, which allows US authorities to compel access to data held by US providers irrespective of its global storage location. This extraterritorial reach creates potential conflicts with EU data protection laws (e.g., GDPR). Beyond legal compliance, escalating geopolitical tensions and trade friction introduce significant operational and financial risks. Potential tariffs threaten cost unpredictability, while the spectre of politically motivated service restrictions underscores the vulnerability of dependence on non-EU infrastructure. These combined legal, operational, and economic pressures make a robust cloud sovereignty strategy essential.
In response, four main approaches have emerged as alternatives or enhancements to standard hyperscaler public clouds. Each offers a distinct approach to cloud sovereignty, with different trade-offs in terms of service breadth, operational complexity, cost predictability, and regulatory alignment. Below is an in‐depth exploration of these four approaches designed to help technology leaders make informed decisions.
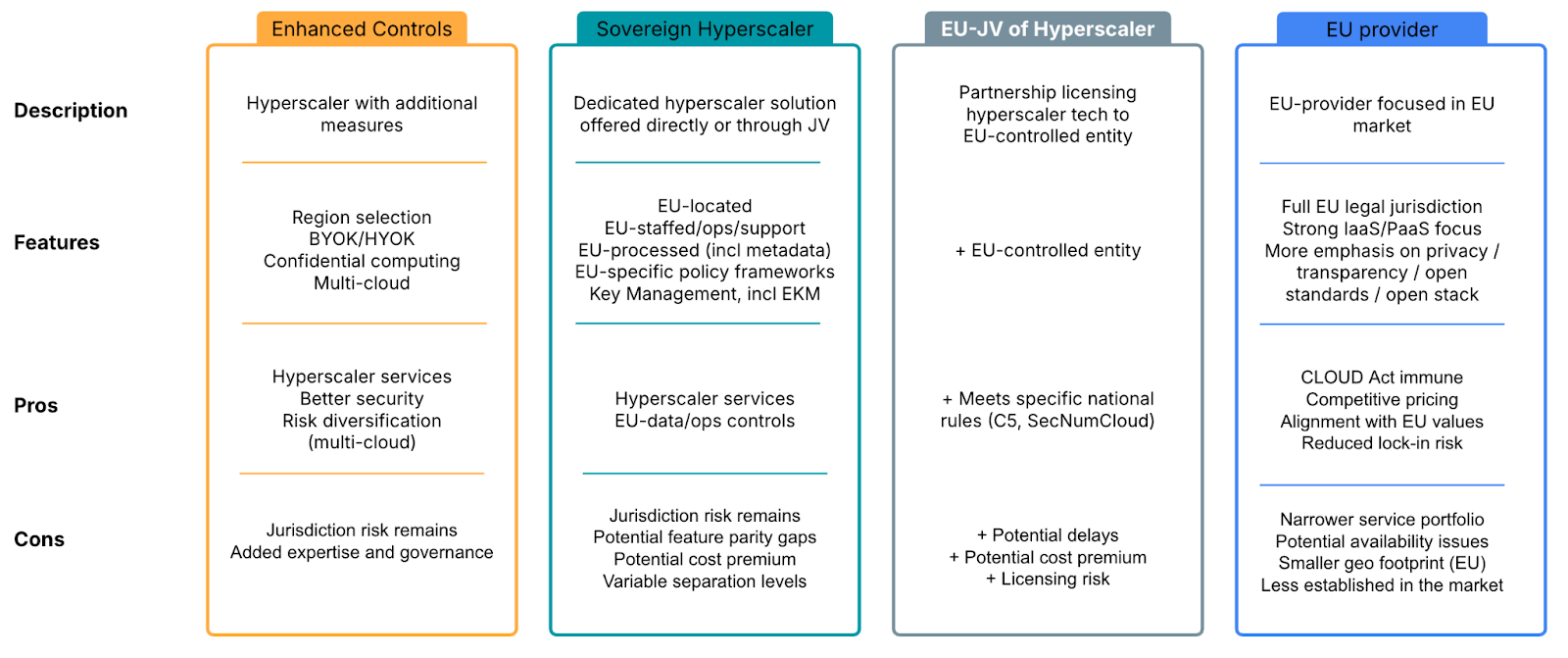
1. Public Cloud with Enhanced Controls
One pathway involves continuing to leverage the extensive infrastructure and advanced services of leading public cloud providers—such as AWS, Microsoft Azure, and Google Cloud—while significantly strengthening security and control through customer-managed measures. This approach aims to mitigate some sovereignty risks by layering additional controls directly managed by the organization. Key elements include:
- Robust Encryption Key Management: Implementing strategies like Bring Your Own Key (BYOK) or Hold Your Own Key (HYOK) where the customer retains greater control over cryptographic keys used to protect their data.
- Strict Data Handling Policies: Enforcing granular policies governing data access, processing, and lifecycle management within the cloud environment.
- Tightened Identity and Access Management (IAM): Utilizing advanced IAM features, strong authentication (MFA), and principles like least privilege to minimize unauthorized access.
- Confidential Computing (where available): Exploring features that protect data even while it is being processed in memory.
While providers offer data residency guarantees within specific EU regions and contractual safeguards such as Standard Contractual Clauses (SCCs) or participation in frameworks like the EU-US Data Privacy Framework (DPF), critical limitations remain: the underlying infrastructure and the service provider itself are typically subject to the jurisdiction of the parent company (often US-based). Therefore, this approach addresses certain compliance aspects but does not fully eliminate risks associated with extraterritorial laws like the US CLOUD Act, nor does it insulate the organization from potential geopolitical impacts affecting the US provider. It is often chosen by organizations prioritizing access to the latest hyperscaler features while accepting these residual risks.
2. Hyperscaler EU Sovereign Offerings
Recognizing the demand for greater assurance, major hyperscalers are introducing dedicated cloud offerings specifically designed for the EU market. These solutions aim to provide enhanced data residency and operational controls compared to standard public cloud regions. Often, this involves commitments around data processing locations (including metadata), stricter controls over operational access (potentially using EU-based personnel for certain support and operational functions), EU-specific policy frameworks, advanced key management options (like External Key Management – EKM), and increased transparency. Examples might include specific sovereign landing zones or dedicated cloud environments marketed under a sovereignty banner (e.g., AWS European Sovereign Cloud, Oracle EU Sovereign Cloud). While owned and ultimately controlled by the hyperscaler parent company, these offerings add layers of technical and operational separation intended to meet specific European regulatory requirements or customer demands. Organizations should carefully evaluate the specific guarantees and operational models offered, as the degree of separation and immunity from foreign jurisdictional reach (like the CLOUD Act) or geopolitical risks can vary and may still be debated. Potential cost premiums may also apply.
3. Joint Ventures (JVs) of Hyperscalers with EU Providers
A distinct approach involves partnerships where hyperscaler technology is licensed to, and operated by, EU-controlled entities. These Joint Ventures (JVs) aim to create high-assurance sovereign clouds by establishing separate European legal entities that manage and deliver the cloud services. Initiatives such as France’s “Bleu” (a collaboration involving Microsoft, Orange, and Capgemini) or “S3NS” (involving Google and Thales) exemplify this model. The core idea is to remove direct US (or other non-EU) jurisdiction from the day-to-day operations and data processing by having an EU entity in control, thus offering a stronger legal shield against extraterritorial laws like the CLOUD Act and potentially greater insulation from US-centric geopolitical events. This structure seeks to combine the technological maturity of hyperscaler platforms with the legal and operational sovereignty provided by an EU-based operator. Potential trade-offs might include a slight lag in feature parity compared to the global hyperscaler platforms and the complexities inherent in managing a JV relationship and licensing terms.
4. EU-Based Cloud Providers
A distinct alternative involves strategically migrating workloads to cloud providers headquartered, operated, and legally domiciled within the European Union. This approach directly addresses core sovereignty concerns by ensuring that both the data and the provider operating the infrastructure fall primarily under EU laws and regulatory frameworks, such as the GDPR. This structure removes exposure to extraterritorial legislation like the US CLOUD Act, simplifies the compliance landscape, and offers greater resilience against geopolitical tensions.
Providers such as OVHcloud (France), Scaleway (France), T-Systems (Germany), and Exoscale (Switzerland/Austria) exemplify this model, offering mature Infrastructure-as-a-Service (IaaS) and increasingly capable Platform-as-a-Service (PaaS) solutions. Their primary appeal lies in providing enhanced data control, a clearer regulatory pathway, and potentially more predictable long-term operating conditions, making them particularly compelling for organizations handling highly sensitive information or operating in sectors with stringent data protection requirements (e.g., public sector, finance, healthcare).
The main trade-off often involves the breadth and depth of available services. While EU providers offer robust core cloud capabilities, they may not match the extensive portfolio of highly specialized PaaS or cutting-edge AI/ML services, nor the rapid innovation pace often associated with US hyperscalers. Furthermore, migrating to a new provider is a significant undertaking, demanding thorough planning, potentially substantial investment, and careful execution to manage complexity and ensure business continuity during the transition.
Leveraging Hybrid and Multi-Cloud Strategies
It is crucial to recognize that these four approaches are not necessarily mutually exclusive. Many organizations adopt a hybrid or multi-cloud strategy, deliberately distributing workloads and data across a mixture of environments to align the placement of each workload with its specific sensitivity, regulatory, performance, and risk tolerance requirements (including legal and geopolitical risks). This strategy involves using different cloud models concurrently – perhaps combining EU-based providers for highly sensitive data requiring strict sovereignty and stability, Hyperscaler EU Sovereign Offerings or JVs for regulated workloads needing specific features, and Public Cloud with Enhanced Controls for less sensitive applications benefiting from the broadest service portfolio. Hybrid architectures (mixing public cloud with private/on-premises) further allow organizations to secure mission-critical data within tightly controlled environments while leveraging public clouds for scalability and innovation. While offering flexibility and risk mitigation (avoiding vendor lock-in), such diversified approaches introduce complexity in governance, security orchestration, cost management, and require sophisticated management tools and cross-platform expertise.
Making the Strategic Choice
In summary, each of the four approaches discussed offers a distinct balance of benefits, risks, and operational demands in light of both legal and geopolitical factors:
- Public Cloud with Enhanced Controls: Prioritizes access to the full range of hyperscaler services and innovation, leveraging customer-managed security (encryption, IAM) to mitigate some risks, but retains fundamental exposure to US jurisdiction (e.g., CLOUD Act) and potential geopolitical/economic volatility affecting the provider.
- Hyperscaler EU Sovereign Offerings: Provide stronger data residency and operational controls (e.g., EU personnel) within the hyperscaler ecosystem, offering improved compliance posture but likely still falling under ultimate US parent company jurisdiction and related risks, potentially at a premium cost.
- Joint Ventures (JVs): Aim for stronger legal insulation from non-EU laws by using an EU entity to operate hyperscaler technology, potentially offering greater sovereignty assurance and stability at the cost of possible feature lags and JV management complexities.
- EU-Based Cloud Providers: Offer the most straightforward path to data sovereignty under EU law, simplified compliance, and insulation from non-EU geopolitical risks, ideal for sensitive data, though potentially with a less extensive portfolio of cutting-edge services compared to global hyperscalers.
Leadership teams should undertake a thorough assessment of their regulatory exposure, technical dependencies, potential cost volatility, and risk tolerance (both legal and geopolitical). Mapping existing cloud usage, categorizing data sensitivity, and forecasting the financial and operational implications of each model are essential steps. Ultimately, the chosen strategy must align with long-term business goals, ensure regulatory compliance, and build the resilience necessary to thrive in an increasingly complex and unpredictable digital environment.
For CIOs and CTOs, this decision goes beyond choosing a provider or technology — it is about crafting an overall cloud strategy that balances innovation with the imperatives of control, compliance, cost predictability, and sustained operational efficiency.
Need help assessing your organization’s specific cloud sovereignty risks and developing a tailored strategy? Contact us today.
